- Our Practice
- Our People
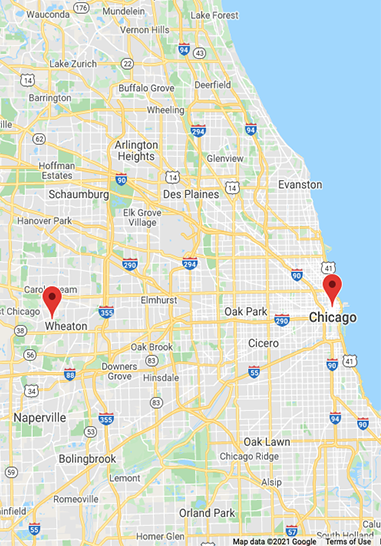
- Our ReachLocal PresenceChicago Office 225 W. Washington St.map Suite 2800 • Chicago, Il 60606
(312) 828 - 9600 • contact us Wheaton Office 301 S. County Farm Roadmap Suite A • Wheaton, Illinois 60187
(312) 828 - 9600 • contact usGlobal Resources